Denial-of-service attack
[3][4] A DDoS attack is analogous to a group of people crowding the entry door of a shop, making it hard for legitimate customers to enter, thus disrupting trade and losing the business money.Criminal perpetrators of DDoS attacks often target sites or services hosted on high-profile web servers such as banks or credit card payment gateways.On September 6, 1996, Panix was subject to a SYN flood attack, which brought down its services for several days while hardware vendors, notably Cisco, figured out a proper defense.[9] Another early demonstration of the DoS attack was made by Khan C. Smith in 1997 during a DEF CON event, disrupting Internet access to the Las Vegas Strip for over an hour.The release of sample code during the event led to the online attack of Sprint, EarthLink, E-Trade, and other major corporations in the year to follow.[11] The record holder was thought to be an attack executed by an unnamed customer of the US-based service provider Arbor Networks, reaching a peak of about 1.7 Tb/s.[13] In July 2021, CDN Provider Cloudflare boasted of protecting its client from a DDoS attack from a global Mirai botnet that was up to 17.2 million requests per second.[15] In the first half of 2022, the Russian invasion of Ukraine significantly shaped the cyberthreat landscape, with an increase in cyberattacks attributed to both state-sponsored actors and global hacktivist activities.The most notable event was a DDoS attack in February, the largest Ukraine has encountered, disrupting government and financial sector services.Particularly, the UK's financial sector saw an increase in DDoS attacks from nation-state actors and hacktivists, aimed at undermining Ukraine's allies.[20] On 14 January 2024, they executed a DDoS attack on Swiss federal websites, prompted by President Zelensky's attendance at the Davos World Economic Forum.[25][26] The hacktivist group SN_Blackmeta claimed the DDoS attack as retribution for American involvement in the Israel–Hamas war, despite the Internet Archive being unaffiliated with the United States government; however, their link with the preceding data leak remains unclear.[43] In November 2017; Junade Ali, an engineer at Cloudflare noted that whilst network-level attacks continue to be of high capacity, they were occurring less frequently.In this scenario, attackers with continuous access to several very powerful network resources are capable of sustaining a prolonged campaign generating enormous levels of unamplified DDoS traffic.APDoS attacks are characterized by: Some vendors provide so-called booter or stresser services, which have simple web-based front ends, and accept payment over the web.[49] Usually powered by a botnet, the traffic produced by a consumer stresser can range anywhere from 5-50 Gbit/s, which can, in most cases, deny the average home user internet access.Application-layer attacks employ DoS-causing exploits and can cause server-running software to fill the disk space or consume all available memory or CPU time.Pulsing zombies are compromised computers that are directed to launch intermittent and short-lived floodings of victim websites with the intent of merely slowing it rather than crashing it.These flood attacks do not require completion of the TCP three-way handshake and attempt to exhaust the destination SYN queue or the server bandwidth.Because of these features, and the potential and high probability of security exploits on network-enabled embedded devices, this technique has come to the attention of numerous hacking communities.The worm propagates through networks and systems taking control of poorly protected IoT devices such as thermostats, Wi-Fi-enabled clocks, and washing machines.[100] Essentially, a sophisticated DDoS attack is lower in cost due to its use of less traffic, is smaller in size making it more difficult to identify, and it has the ability to hurt systems which are protected by flow control mechanisms.The UPnP router returns the data on an unexpected UDP port from a bogus IP address, making it harder to take simple action to shut down the traffic flood.Many devices, including some residential routers, have a vulnerability in the UPnP software that allows an attacker to get replies from UDP port 1900 to a destination address of their choice.With a botnet of thousands of devices, the attackers can generate sufficient packet rates and occupy bandwidth to saturate links, causing the denial of services.If a mob of customers arrived in the store and spent all their time picking up items and putting them back, but never made any purchases, this could be flagged as unusual behavior.This can happen when an extremely popular website posts a prominent link to a second, less well-prepared site, for example, as part of a news story.The result is that a significant proportion of the primary site's regular users – potentially hundreds of thousands of people – click that link in the space of a few hours, having the same effect on the target website as a DDoS attack.In one example, in July 2019, Austin Thompson, aka DerpTrolling, was sentenced to 27 months in prison and $95,000 restitution by a federal court for conducting multiple DDoS attacks on major video gaming companies, disrupting their systems from hours to days.[143] In January 2019, Europol announced that "actions are currently underway worldwide to track down the users" of Webstresser.org, a former DDoS marketplace that was shut down in April 2018 as part of Operation Power Off.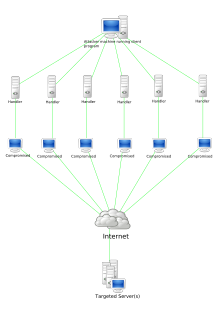


DOS (disambiguation)computingcyber-attackservicesnetworkfloodingIP addressweb serverscredit cardpayment gatewaysRevengeblackmailhacktivismSYN floodDEF CONLas Vegas StripSprintEarthLinkE-TradeGoogle CloudArbor NetworksAmazon Web ServicesCloudflareMirai botnetYandexRussian invasion of Ukrainenation-stateArchive of Our OwnAnonymous SudanOrganization for Transformative WorksBitcoinNoName057slow DoS attacksPresident ZelenskyDavos World Economic ForumHTTP/2GoogleMinecraft game serversInternet ArchiveIsrael–Hamas warbandwidthmalwareingress filteringIP address spoofingterabit per secondUDP floodingSYN floodingcloud-hostedautoscalingapplication-layerAkamai TechnologiesOSI modelabstraction layersOpen Systems InterconnectionInternational Organization for Standardizationpresentation layerbotnetadvanced persistent threatDDoS mitigationStresserhidden Markov modelUnited States Computer Emergency Readiness Teamnetwork performanceMyDoomSlowlorisStacheldrahtclient programzombie agentsOperation PaybackAnonymousLow Orbit Ion CannonHigh Orbit Ion CannonexploitsCPU timefork bombapplication firewallsSlowDroidcloud computingtrojanzombie agentbotnetsIP spoofingsmurf attacksfraggle attacksSYN floodsScript kiddiesextortioninternet of thingsthree-way handshakeSYN cookiesTCP SYNHTTP POST headerApache HTTP Serveropen sourceUniform Resource Identifierssmurf attackbroadcast addressPing floodUnix-likePing of deathBlackNursecomputer networkscorrupt dataWinNukeNetBIOSWindows 95Blue Screen of Deathpeer-to-peerpeer-to-peer file sharingroutersnetworking hardwarevulnerabilitiesfirmwareBrickerBotHewlett-PackardInternet Protocol address spoofingICMP echo requestMemcachedCHARGENBitTorrentSNMPv2Steam ProtocolSimple Network Management ProtocolNetwork Time Protocolcomputer wormattacked Dyn