Burroughs B6x00-7x00 instruction set
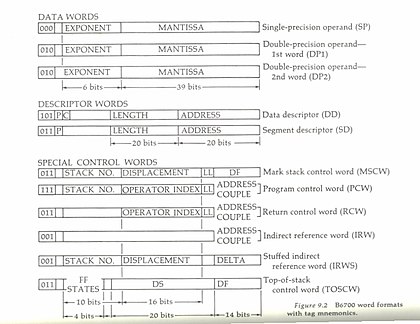
Some of the code density was due to moving vital operand information elsewhere, to 'tags' on every data word or into tables of pointers.The architecture only distinguishes single and double precision numbers – integers are just reals with a zero exponent.NAMC simply loads the address couple onto the top of the stack as an IRW (with the tag automatically set to 1).Static branches (BRUN, BRFL, and BRTR) used two additional syllables of offset.As a result, code was much denser (had better entropy) than a conventional RISC architecture in which each operation occupies four bytes.Odd-tagged words are created and used directly by the hardware and represent a program's execution state.The normal IRW simply stores an address couple to data on the current stack.Functions (value-returning routines) are implicitly entered by operators such as value call (VALC).This means that asynchronous processes still have access to the D[2] environment as implied in ALGOL program code.The ability to link a data structure into the display register address scope implemented object orientation.On other systems, the compiler might build its symbol table in a similar manner, but eventually the storage requirements would be collated and the machine code would be written to use flat memory addresses of 16-bits or 32-bits or even 64-bits.And indeed, this was reflected in the form of the VALC instruction (value call) that loaded an operand onto the stack.The address part of the VALC operation thus reserved just three bits for that purpose, with the remainder being available for referring to entities at that and lower levels.Much more important is that this method meant that many errors available to systems employing flat addressing could not occur because they were simply unspeakable even at the machine code level.Offsets from a specified D-register would be checked by the hardware against the stack frame bound: rogue values would be trapped.In any case, the tagging of all memory words provided a second level of protection: a misdirected assignment of a value could only go to a data-holding location, not to one holding a pointer or an array descriptor, etc.The Load instruction could find itself tripping on an indirect address, or worse, a disguised call to a call-by-name thunk routine.